Over the years, the number of cell phones has increased rapidly. In this age, almost everyone has a cell phone and, in particular, a smartphone. Phones have made life much easier, there is effective communication between people, and it has improved numerous lives including the growth of Tech billionaires and employment opportunities for many people.
Related: It’s High Time You Started Worrying: The Rich Are Becoming Preppers
We use our phones for almost everything from booking a flight or an Uber to purchasing different products in an online store for our use. But with every object, there is always a looming shadow besides it. By use of a phone a person can store his personal details in an account without going through the hustle of using a computer. Although this seems cool and perhaps efficient, it has some limitations because of the presence of online ‘vultures’ ready to pounce and feed on your details if your phone is unsecured.
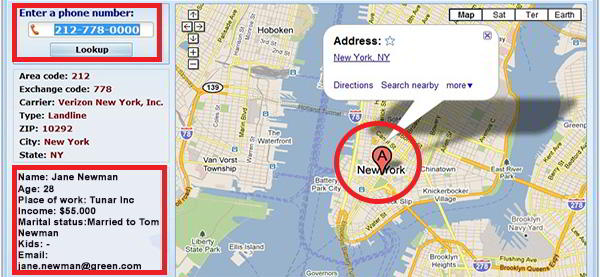
The number of hackers has increased proportionally with the increase in the number of smartphones. All that a hacker requires can be your phone number to infiltrate your privacy and mess up your life. This has also increased the vulnerability of phones over the years.
We buy smartphones every other day, and the rate at which new models and features are released is quite high, but most of us never take the time to check if our phones are secured or not. A high percentage of people are always on their phones on the better part of the day. This makes it easier for hackers to target phones which also have minimal security compared to computers.
In the recent past, numerous cases of phone hacks had been recorded, and similar attacks carried out by NSO group (which disposes of surveillance software to snoop on people’s emails and messages) in the US had been reported.
Phone surveillance and hacking had been known as one of the main causes of security breaches in the country. To show how grave the matter is, Edward Snowden had to seek asylum in Russia for reporting on the massive surveillance of the government on its citizens. With these vulnerabilities, the question arises: how does one protect their phone from hacking and being monitored?
Ways to Protect your Phone
- Buying well-secured smartphones
As prevention is better than cure, the first step in securing your phone is by purchasing a phone that is well protected from hackers. With the increased cases of phone surveillance and hacking, phone companies had to step up and include security design upgrades for their phones so that their customers may have some peace of mind.
Although this has been done, there are other phone companies who take minimal steps in securing their phones and leave this responsibility to the phone buyers as expressed in their terms of service. When looking for a new phone, it is not enough to only consider the quality of the camera, the screen size of the phone, the storage capacity and the battery capacity.
You first need to examine if the phone is secure from external attacks from hackers and the ease with which the phone can be monitored.
- Installing phone security applications and software
All smartphones have online stores with millions of applications. Android phones have the Google Play store, Windows phones have the Microsoft store, and iPhone or Apple phones have the app store. You can secure your phone by searching in the stores for security apps.
The availability of many security apps enables you to specify on the type of security you require. Another advantage is that most of these apps are free so you don’t have to dig into your pockets for funds to be used on purchasing the apps. It is also advisable to install the apps from the official, well-known app stores of the smartphone platforms.
When you get a ‘security’ application from a third party, there are high chances that the app may be a virus or a gateway for hackers to gain access into your phone system. Also, when installing an app regardless of the category, it is advisable to read the permissions required by the application because some apps require permissions that make your phone vulnerable to attacks.
Some of the features of these security apps include protecting your phone platform from threats such as unsecured links, unsecured networks, malicious applications, and viruses.
- Encrypt your phone data
This refers to the process of storing your phone data in a scrambled, unreadable form. By encrypting your phone, you can protect sensitive information contained in your phone. A hacker or any other person who wants to put you under surveillance will not be able to gain access to your data without your authorization or the encryption code to decrypt the data.
After encrypting your data, your phone can only be unlocked when you enter the phone’s password. Although the effect that comes with encryption is that your phone might have slightly lower performance because of the need to decrypt every time you want to access your data, it is one of the most efficient ways of keeping your phone secure, and the protection is worth it. The encryption settings can be easily accessed from your phone’s settings tab.
- Update your operating system
No matter the type of operating system your phone is running, it is of great importance to always update the software. That’s because with every update there is an improvement of your phone’s security features and the developers work hard in closing any security loopholes that keep arising with every upgrade.
The vulnerability of your phone is reduced, and your phone becomes more secure. Also, by upgrading you can be in control by determining what type of permissions the applications you install will be able to access on your phone.
- Not Rooting or Jailbreaking your device
The process of rooting or jailbreaking your device has always been considered as a way of gaining freedom for your device, but sometimes freedom comes at a price. If you are not an experienced user, the process can prove deadly to your phone’s security. It is like opening the lock and ushering in hackers for a cup of tea because it reduces the amount of time they would require to get access to your phone.
When you root your phone, you remove the available protection and trade it for added functionalities that may add nothing to your protection. Sometimes it’s better to have device limitations if it guarantees your phone’s security.
- Backing up your phone’s data and set up remote wipe
It is of great importance to always have a backup of your data either by syncing your device files to an online account, cloud storage or by connecting your phone to your computer and moving your data to a PC to preserve your files. This should be done in case your phone falls into the wrong hands and the person decides to snoop over your data.
By enacting the remote wipe feature, you will be able to clear all data remotely. Hence, the person won’t have anything on you, and you can also determine the location of your phone in case you lose it. This makes your phone more secure and less vulnerable to surveillance and attack from hackers.
How to Test for Protection
There are various ways to test if your phone is protected from malware, hackers and surveillance but the best methods are:
- Check if your phone behaves unlike the normal way. For example: when apps open without your consent, when the phone starts sending text messages or starting a phone call by itself then your phone might be compromised and there is need for you to seek for protection.
- If you notice strange charges on your phone that you did not approve, then that may show that your phone is secure.
- Another way is by running an antivirus app on your phone which may show if there is any malware available on your phone.
Whenever you feel like your phone is not secure, take the necessary step and secure it before it’s too late.
Conclusion
There is need for the government to be involved in securing the privacy of its citizens by enacting laws and policies to deal with hackers. Also, instead of carrying out surveillance on its citizens, they should discourage agencies and organizations that carry out surveillance and monitoring services. Above all, the process of securing your phone and your privacy begins with YOU!
You may also like:
 How To Make A Tin Can Directional WiFi Antenna to Extend your Communication after an EMP
How To Make A Tin Can Directional WiFi Antenna to Extend your Communication after an EMP
SHTF Antibiotics (True Story)(Video)















How about don’t use your phone? I don’t have a cell. Just a thought. We lived without these things before.
I miss those days. The microwaves used by these phones are very dangerous. I had a friend that worked for a cell company and he said that the microwaves are the cause of the bee hive populations dying off. He quit the company and refuses to have one. This person could help you understand what’s going on. https://www.google.com/amp/s/ascendingstarseed.wordpress.com/2013/10/27/barrie-trower-the-cooking-of-humanity/amp/
TogetherWeStand, this link is gone, “ascendingstarseed.wordpress.com is no longer available.
This site has been archived or suspended for a violation of our Terms of Service.
For more information and to contact us please read this support document”.
My $14.99 old as the hills no frills pay as you go flip phone works well.. Used for Emergency calls only.. the technology itself is so old the new wave hacker doesn’t use it..
Janeka; Excellent! ☺
Stay away from the smart phones. The microwave exposure isn’t as bad with a flop phone. 4G going to 5G means much more exposure to microwaves.
https://www.google.com/amp/s/ascendingstarseed.wordpress.com/2013/10/27/barrie-trower-the-cooking-of-humanity/amp/
Take said cell phone and place on hard surface such as concrete or asphalt. Grab a blunt object such as a hammer and commence beating the said cell phone into a thousand individual pieces and viola no more tracking device and or spying contraption.
Or exposure to the microwaves they expose a person to. 5G is coming. Stronger microwaves. Thinning the herd they are.
https://www.google.com/amp/s/ascendingstarseed.wordpress.com/2013/10/27/barrie-trower-the-cooking-of-humanity/amp/
Right on
Cell phones work on MICROWAVES. 5G means stronger microwave signal. Who cares who is listening in on you if you going to die anyways.
https://www.google.com/amp/s/ascendingstarseed.wordpress.com/2013/10/27/barrie-trower-the-cooking-of-humanity/amp/
“..the developers work hard in closing any security loophole..”
Except when they create ways for tptb to have unlimited access to your accounts, data, phone conversations, location, etc, etc, etc…ad infinitum.
The hackers aren’t the real danger..the government that pays those hackers are.
It is bound that London, the capital and largest metropolitan area inside UK is additionally its largest urban zone.
But, whenever a homeowner does not pay their assessments, it’s the management company’s responsibility to get those funds.
Instead, do not forget that students are generally less fussy than other tenants,
so as long as it is all totally clean and functional you do not need to spend a lot of money on making
your premises in a luxury abode.
Huh?
4G and 5G cell operate on the same frequency… last ive read. Yes it’s “microwave” about 1.8 or around 2ghz. But a cell phone transmits less power than almost all forms of push to talk radio. There won’t be more microwaves in the air, just a different signal modulation that allows more data to be transferred in the 1’s and 0’s. Better signal processing in the phones etc.
I may be mistaken, but under the heading ‘how to test for protection’. Second dot. Should it be ‘ is NOT secure’?
EVERY smartphone has built in back doors that no security measures can stop nor detect.
Towers to phone pings will show your exact location, path traveled, and what destination you are at and for how long.
Go tot he bar and SOMEONE will know.
Get a VD test/treatment and SOMEONE will know.
Go to a political rally and certainly SOMEONE will know.
And most of them never asked for your permission.
6G is about to come out soon too.
Oh remember that 6 foot spacing during covid?
Tracking needs no closer than 6 feet from the nearest cell phone to track you properly.
Duration of exposure is very different with a push to talk radio it is a sudden burst not a constant. Not to mention you’re not walking through push-to-talk soup all the time. With cell phones you are under constant pressure from the EMF on your body. Please, spend some time understanding the topic as your comments indicate you know something but we need to grow that knowledge base a little bit more
???
I don’t own nor do I want a cell phone that does everything but, the dishes. In case of an EMP strike, they will all go down anyway.
This article didn’t really present anything but common knowledge. There is no way to keep Uncle Sam out of it; Apple and Google gave them easier access in 2020 for “covid tracking”, so if you’ve updated since then they can access your phone instantly (probably no warrant needed now). As for hackers, the easiest way to stop them is to not click on sketchy links and click bait. It is terrifying how easy it is to hack a phone or a whole system. Too many people don’t know how to tell if a link is legitimate and just open the door wide.
Simple Solution here Folks………………DON’T OWN A CELLPHONE!
I don’t have one and never will!